|
This section on firewalls prepared by Dominick Diorio
Introduction to Firewalls
A firewall can significantly improve security for a site. The trick is not to
compromise important services the site needs to perform. A firewall is comprised
of a system, or systems that regulates access between two networks.
Conceptually, there are two ways this regulation can be accomplished. First,
a firewall can exist to block traffic, and secondly, it can permit traffic to
flow.
A high level of protection is provided by proxy servers. A proxy server is a
component of a firewall that controls how internal users access outside
resources, and how outside resources access the internal network. Sometimes the
proxy blocks all outside connections and only allows internal users to access
outside resources. The only packets allowed back through the proxy are those
that return responses to requests from inside the firewall.
Firewalls can be described as a choke point through which all internal and
external traffic is controlled. You can monitor and block access at these choke
points.
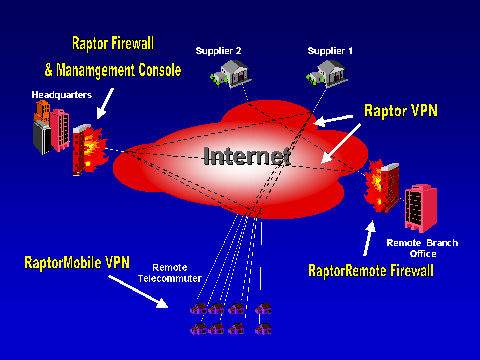
http://www.axent.com/product/rsbu/firewall/R6brochure.htm
Types of Firewalls
Screening Routers
We could call any device that controls network traffic for security reasons
as a firewall. Three major types of firewalls will be discussed. These use
different methods of protecting networks. The first type, screening routers, are
basic firewall devices that are built on routers. These perform packet
filtering. Screening routers can look at the incoming computer's port number or
IP address and filter based on that information. For example, you can block all
applications except HTTP services.
Proxy Server Gateway
The second type of firewall is a proxy server gateway. A gateway relays
messages from internal clients to external services. The proxy service changes
the IP address of the client packets to hide internal information from the
Internet. Using proxies reduces the threat from hackers that might monitor
network traffic to learn information about computers on your internal network.
There are two types of proxy servers.
Circuit-Level Gateway
First is the circuit-level gateway. This type of proxy server provides a
controlled network connection between internal clients and external systems. A
virtual circuit exists between the internal client and the proxy server.
Internet requests go through this circuit to the proxy server, and then the
proxy server delivers those requests to the Internet. This is done after
changing the IP address to hide it from the outside. External users only see the
IP address of the proxy server. Responses are then received by the proxy server
and sent back through the circuit to the client. Even though traffic is allowed
to flow in both directions, external systems never see the internal systems.
Application-Level Proxy Server
The second type of proxy server is the application-level proxy server. This
provides all the basic proxy features. In addition, it also provides extensive
packet analysis. When packets from the outside arrive at the firewall, they are
examined and judged to determine if the security policy allows the packet to
enter into the internal network. This means that server not only evaluates the
IP address, it also looks at the data in the packets to stop malicious packets
from entering the network.
Stateful Inspection Techniques
Service Strategies Inc. defines stateful inspection as: Analysis of data
within the lowest levels of the protocol stack and comparing the current session
to previous ones in order to detect suspicious activity. Unlike application
level gateways, stateful inspection uses business rules defined by the user and
therefore does not rely on predefined application information. Stateful
inspection also takes less processing power than application level analysis.
Stateful inspection firewalls do not recognize specific applications and thus
are unable to apply different rules to different applications.
http://www.ssimail.com/Glossary.htm#stateful inspection
Firewall features to look for
After the decision is made to use a firewall, you need to decide on the
specific features needed. The following is a list from the National Institute of
Standards and technology (http://csrc.ncsl.nist.gov/nistpubs/800-10) and can be
used as general guidelines:
 | The firewall should be able to support a ``deny all services except those
specifically permitted'' design policy, even if that is not the policy used.
 | The firewall should support your security policy, not impose one.
 | The firewall should be flexible; it should be able to accommodate new
services and needs if the security policy of the organization changes.
 | The firewall should contain advanced authentication measures or should
contain the hooks for installing advanced authentication measures.
 | The firewall should employ filtering techniques to permit or deny services
to specified host systems as needed.
 | The IP filtering language should be flexible, user-friendly to program, and
should filter on as many attributes as possible, including source and
destination IP address, protocol type, source and destination TCP/UDP port, and
inbound and outbound interface.
 | The firewall should use proxy services for services such as FTP and TELNET,
so that advanced authentication measures can be employed and centralized at the
firewall. If services such as NNTP, X, http, or gopher are required, the
firewall should contain the corresponding proxy services.
 | The firewall should contain the ability to centralize SMTP access, to reduce
direct SMTP connections between site and remote systems. This results in
centralized handling of site e-mail.
 | The firewall should accomodate public access to the site, such that public
information servers can be protected by the firewall but can be segregated from
site systems that do not require the public access.
 | The firewall should contain the ability to concentrate and filter dial-in
access.
 | The firewall should contain mechanisms for logging traffic and suspicious
activity, and should contain mechanisms for log reduction so that logs are
readable and understandable.
 | If the firewall requires an operating system such as UNIX, a secured version
of the operating system should be part of the firewall, with other security
tools as necessary to ensure firewall host integrity. The operating system
should have all patches installed.
 | The firewall should be developed in a manner that its strength and
correctness is verifiable. It should be simple in design so that it can be
understood and maintained.
 | The firewall and any corresponding operating system should be updated with
patches and other bug fixes in a timely manner. | | | | | | | | | | | | | |
I've added the following to their list:
 | Plan for complete system failures, and have backups in the event of an
attack
 | Encrypt outbound traffic. This can hide both the identity of the sending
machine, as well as the information itself.
 | Ensure adequate memory resources. You must have enough RAM to run all
available programs and resources placed on the machine. Otherwise, the system
may shut down from its own overload. Additionally, a denial-of-service attack
can be easily implemented.
 | Loadbalancing | | | |
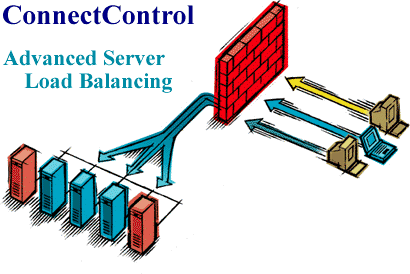
http://www.checkpoint.com/products/floodgate-1/cc.html
Financial Considerations
You might think a firewall would be an expenditure in addition to other
necessary purchases, and therefore increment the overall cost of the system. On
the contrary, a firewall can actually reduce the overall cost of the system by
permitting all the security related software to be located in one place, versus
having to locate these systems on each individual computer. For example,
password software could be located at the firewall as opposed to each unit that
needed to be accessed from the Internet.
Firewall Policies
If an intruder can find a hole in the firewall, then the firewall has failed.
Once a hacker is in, the internal network is at their mercy. If they hijack an
account, then all the resources available to that account are at risk. No
firewall can protect against poor firewall policies. If a password is obtained
by someone outside the system because a user did not hide it properly, then the
security is at risk. If an internal user dials out through an unauthorized
connection, an attacker could subvert your network through this backdoor.
Therefore, you must implement a firewall policy in advance of implementing the
product. These policies should be made as part of an overall security policy.
All network traffic to and from outside networks must be first filtered, then
pass through the firewall.
Additionally, the firewall should not be used for file storage or to run
programs, except for those required by the firewall. Similarly, no services
should be run on the firewall except those specifically required to provide
firewall services. Finally, no passwords or internal addresses to be sent across
the firewall.
This security policy implemented needs to be flexible. This flexibility is
needed to accommodate the overall change in the organization, as well as the
change currently taking place in the internet itself.
Statistics on Network Use and Misuse
When all access to and from the outside passes through a firewall, the
firewall can keep track of valuable statistics about usage. The firewall should
have alarms that go off when irregular activity occurs. Statistics should be
kept, and be able to give an indication if the system is being probed or
attacked. This can tell us whether or not the firewall has had to withstand the
attacks. These statistics can also be used in network requirement studies and
system analysis scenarios. These then can drive cost benefit analysis.
http://www.checkpoint.com/products/floodgate-1/index.html
http://www.checkpoint.com/products/floodgate-1/index.html
From the Raptor product: http://www.raptor.com/
Comprehensive Logging and Reporting
The Raptor Firewall log files contain information that includes: session
duration; byte counts; full URLs; user names and authentication methods.
Administrators can use this information to generate detailed statistical and
session trend reports ... or they can export to databases to perform custom
analysis.
Problems / Other Considerations
Unavailable Services
Unfortunately, firewalls might block services that users want, such as
TELNET, FTP, X Windows, etc.
Back Doors
If back doors exist around the firewall, the firewall is of little use. For
example, modem access might be permitted into a site, and allow the firewall to
be bypassed.
Insider Attacks
Firewalls generally protect inside systems from outsiders. They do not
provide effective protection from insiders' threats. Firewalls should only be
expected to accomplish the tasks for which they were designed. Again, they need
to be used in the context of an overall security policy.
Viruses
Users might still download virus-laden software from the internet and
transfer it via e-mail. These programs can be encoded or compressed in many ways
and hide from the firewall. Viruses should be handled with a separate policy and
viral software.
Throughput
Firewalls, unfortunately, can act as a bottleneck. If the system is
configured such that all traffic is routed through and examined by the firewall,
then the whole system might have to move at the speed of the slowest piece - the
firewall.
Remote Network Connections
Taken from http://csrc.ncsl.nist.gov/nistpubs/800-10/
In addition to dial-in/dial-out connections, the use of Serial Line IP (SLIP)
and Point-to-Point Protocol (PPP) connections need to be considered as part of
the policy. Users could use SLIP or PPP to create new network connections into a
site protected by a firewall. Such a connection is potentially a backdoor around
the firewall.
Authenticating remote access users
Taken from http://csrc.ncsl.nist.gov/nistpubs/800-10/
Remote users are those who originate connections to site system from
elsewhere on the Internet. These connections could come from any location on the
Internet, from dial-in lines, or from authorized users on travel or working from
home. Regardless, all such connections should use the advanced authentication
service of the firewall to access systems at the site. Policy should reflect
that remote users may not access systems through unauthorized modems placed
behind the firewall. There must be no exceptions to this policy, as it may take
only one captured password or one uncontrolled modem line to enable a backdoor
around the firewall.
Such a policy has its drawbacks: increased user training for using advanced
authentication measures, increased expense if remote users must be supplied with
authentication tokens or smartcards, and increased overhead in administering
remote access. But, it does not make sense to install a firewall and at the same
time not control remote access.
From www.clark.net/pub/mjr/pubs/fwfaq
- Abuse of Privilege:
When a user performs an action that they should not have, according to
organizational policy or law.
Access Control Lists:
Rules for packet filters (typically routers) that define which packets to
pass and which to block.
Access Router:
A router that connects your network to the external Internet. Typically,
this is your first line of defense against attackers from the outside Internet.
By enabling access control lists on this router, you'll be able to provide a
level of protection for all of the hosts "behind" that router,
effectively making that network a DMZ instead of an unprotected external LAN.
Application-Level Firewall:
A firewall system in which service is provided by processes that maintain
complete TCP connection state and sequencing. Application level firewalls often
re-address traffic so that outgoing traffic appears to have originated from the
firewall, rather than the internal host.
Authentication:
The process of determining the identity of a user that is attempting to
access a system.
Authentication Token:
A portable device used for authenticating a user. Authentication tokens
operate by challenge/response, time-based code sequences, or other techniques.
This may include paper-based lists of one-time passwords.
Authorization:
The process of determining what types of activities are permitted. Usually,
authorization is in the context of authentication: once you have authenticated a
user, they may be authorized different types of access or activity.
Bastion Host:
A system that has been hardened to resist attack, and which is installed on
a network in such a way that it is expected to potentially come under attack.
Bastion hosts are often components of firewalls, or may be "outside"
Web servers or public access systems. Generally, a bastion host is running some
form of general purpose operating system (e.g., Unix, VMS, NT, etc.) rather than
a ROM-based or firmware operating system.
Challenge/Response:
An authentication technique whereby a server sends an unpredictable
challenge to the user, who computes a response using some form of authentication
token.
Chroot:
A technique under Unix whereby a process is permanently restricted to an
isolated subset of the filesystem.
Cryptographic Checksum:
A one-way function applied to a file to produce a unique
"fingerprint" of the file for later reference. Checksum systems are a
primary means of detecting filesystem tampering on Unix.
Data Driven Attack:
A form of attack in which the attack is encoded in innocuous-seeming data
which is executed by a user or other software to implement an attack. In the
case of firewalls, a data driven attack is a concern since it may get through
the firewall in data form and launch an attack against a system behind the
firewall.
Defense in Depth:
The security approach whereby each system on the network is secured to the
greatest possible degree. May be used in conjunction with firewalls.
DNS spoofing:
Assuming the DNS name of another system by either corrupting the name
service cache of a victim system, or by compromising a domain name server for a
valid domain.
Dual Homed Gateway:
A dual homed gateway is a system that has two or more network interfaces,
each of which is connected to a different network. In firewall configurations, a
dual homed gateway usually acts to block or filter some or all of the traffic
trying to pass between the networks.
Encrypting Router:
see Tunneling Router and Virtual Network Perimeter.
Firewall:
A system or combination of systems that enforces a boundary between two or
more networks.
Host-based Security:
The technique of securing an individual system from attack. Host based
security is operating system and version dependent.
Insider Attack:
An attack originating from inside a protected network.
Intrusion Detection:
Detection of break-ins or break-in attempts either manually or via software
expert systems that operate on logs or other information available on the
network.
IP Spoofing:
An attack whereby a system attempts to illicitly impersonate another system
by using its IP network address.
IP Splicing / Hijacking:
An attack whereby an active, established, session is intercepted and
co-opted by the attacker. IP Splicing attacks may occur after an authentication
has been made, permitting the attacker to assume the role of an already
authorized user. Primary protections against IP Splicing rely on encryption at
the session or network layer.
Least Privilege:
Designing operational aspects of a system to operate with a minimum amount
of system privilege. This reduces the authorization level at which various
actions are performed and decreases the chance that a process or user with high
privileges may be caused to perform unauthorized activity resulting in a
security breach.
Logging:
The process of storing information about events that occurred on the
firewall or network.
Log Retention:
How long audit logs are retained and maintained.
Log Processing:
How audit logs are processed, searched for key events, or summarized.
Network-Level Firewall:
A firewall in which traffic is examined at the network protocol packet
level.
Perimeter-based Security:
The technique of securing a network by controlling access to all entry and
exit points of the network.
Policy:
Organization-level rules governing acceptable use of computing resources,
security practices, and operational procedures.
Proxy:
A software agent that acts on behalf of a user. Typical proxies accept a
connection from a user, make a decision as to whether or not the user or client
IP address is permitted to use the proxy, perhaps does additional
authentication, and then completes a connection on behalf of the user to a
remote destination.
Screened Host:
A host on a network behind a screening router. The degree to which a
screened host may be accessed depends on the screening rules in the router.
Screened Subnet:
A subnet behind a screening router. The degree to which the subnet may be
accessed depends on the screening rules in the router.
Screening Router:
A router configured to permit or deny traffic based on a set of permission
rules installed by the administrator.
Session Stealing:
See IP Splicing.
Trojan Horse:
A software entity that appears to do something normal but which, in fact,
contains a trapdoor or attack program.
Tunneling Router:
A router or system capable of routing traffic by encrypting it and
encapsulating it for transmission across an untrusted network, for eventual
de-encapsulation and decryption.
Social Engineering:
An attack based on deceiving users or administrators at the target site.
Social engineering attacks are typically carried out by telephoning users or
operators and pretending to be an authorized user, to attempt to gain illicit
access to systems.
Virtual Network Perimeter:
A network that appears to be a single protected network behind firewalls,
which actually encompasses encrypted virtual links over untrusted networks.
Virus:
A replicating code segment that attaches itself to a program or data file.
Viruses might or might not not contain attack programs or trapdoors.
Unfortunately, many have taken to calling any malicious code a
"virus". If you mean "trojan horse" or "worm", say
"trojan horse" or "worm".
Worm:
A standalone program that, when run, copies itself from one host to another,
and then runs itself on each newly infected host. The widely reported
"Internet Virus" of 1988 was not a virus at all, but actually a worm.
Resources:
www.clark.net/pub/mjr/pubs/fwfaq
http://csrc.ncsl.nist.gov/nistpubs/800-10/
- ftp://ftp.greatcircle.com/pub/firewalls/index.html
- http://sunsite.unc.edu/LDP/HOWTO/Firewall-HOWTO.html
- http://www.clark.net/pub/mjr/pubs/index.shtml
- ftp://net.tamu.edu/pub/security/TAMU/
- http://www.cs.purdue.edu/coast/firewalls/
Visit other great pages on:
Computers & Technology
|