- for private-key authentication
- have an on-line server trusted by all clients
- server has a unique secret key shared with each client
- server negotiates keys on behalf of clients
- use private key encryption
Here use a trusted intermediary, whom all parties trust, to mediate the establishment of secure communications between them. Must trust intermediary not to abuse the knowledge of all session keys.
- a trusted key server system developed by MIT
- provides centralised third-party authentication in a distributed network
- access control may be provided for
- each computing resource
- in either a local or remote network (realm)
- has a Key Distribution Centre (KDC), containing a database of:
- principles (customers and services)
- encryption keys
One of the best known and most widely implemented trusted third party key distribution systems. Still mostly limited to use within a single organisation though.
- a basic third-party authentication scheme
- KDC provides non-corruptible authentication credentials (tickets or tokens)
- user initially negotiates with KDC to identify self
- can subsequently request access to other services
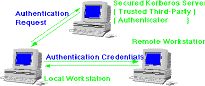
- user requests an initial ticket from KDC
- used as basis for all remote access requests

- user requests access to a remote service
- obtains a ticket from KDC protected with remote key
- sends ticket with request to remote server

- currently have two Kerberos versions
- 4 : restricted to a single realm
- 5 : allows inter-realm authentication, in beta test
- Kerberos v5 is an Internet standard
- specified in RFC1510, and used by many utilities
- to use Kerberos
- need to have a KDC on your network
- need to have Kerberised applications running on all participating systems
- major problem - US export restrictions
- Kerberos cannot be directly distributed outside the US in source format (& binary versions must obscure crypto routine entry points and have no encryption)
- else crypto libraries must be reimplemented locally