- message authentication is concerned with:
- protecting the integrity of a message
- validating identity of originator
- non-repudiation of origin (dispute resolution)
To now, have been concerned with protecting message content (ie secrecy) by encrypting the message. Will now consider how to protect message integrity (ie protection from modification), as well as confirming the identity of the sender. Generically this is the problem of message authentication, and in eCommerce applications is arguably more imprtant than secrecy.
- authenticator, signature, or message authentication code (MAC)
- electronic equivalent of a signature on a message
- sent along with the message
- is generated via some algorithm which depends on both the message and some (public or private) key known only to the sender and receiver
- message may be of any length
- MAC may be of any length, but more often is some fixed size
- this requires the use of some hash function
- to condense the message to the required size
- if this is not acheived by the authentication scheme
- need to consider replay problems with message and MAC
- require a message sequence number, timestamp or negotiated random values
In general, want to send an "electronic signature" along with the message to validate its contents, and the senders identity. Unless the message is processed in a way that provides both encryption and authentication (as when a chaining mode is used with a block cipher), the electronic signature is separate from the encrypted message. Unless the amount of information sent is to be doubled, some means is needed to create a "digest" (MAC) of the message of a suitable, fairly small, size.
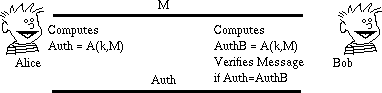
show here we see Alice sending both a message, and the signature (Auth) to Bob. Bob recomputes the signature on the message as he received it, and confirms that it is the same as the one Alice sent him. If so, the message is assumed to be unmodified.
- if a message is being encrypted using a session key known only to the
sender and receiver, then the message may also be authenticated
- since only sender or receiver could have created it
- any interference will corrupt the message (provided it includes sufficient redundancy to detect change)
- but this does not provide non-repudiation since it is impossible to prove who created the message
As mentioned above, if a message is sent encrypted using a chaining mode of a block cipher (CBC or CFB) then implicitly the message is also authenticated, since any external modification would corrupt the decryption, and since only the sender & reciever supposedly know the key used. However since the algorithm is symmtric, there is no way to prove to a 3rd party who did what.
- message authentication may also be done using the standard modes of use
of a block cipher
- sometimes do not want to send encrypted messages
- can use either CBC or CFB modes and send final block, since this will depend on all previous bits of the message
- no hash function is required, since this method accepts arbitrary length input and produces a fixed output
- usually use a fixed known IV
- this is the approached used in Australian EFT standards AS8205
- major disadvantage is small size of resulting MAC since 64-bits is probably too small
Can also use block cipher chaining mdoes to create a separate authenticator, by just sending the last block. However this suffers from being a bit too small for acceptable use today.