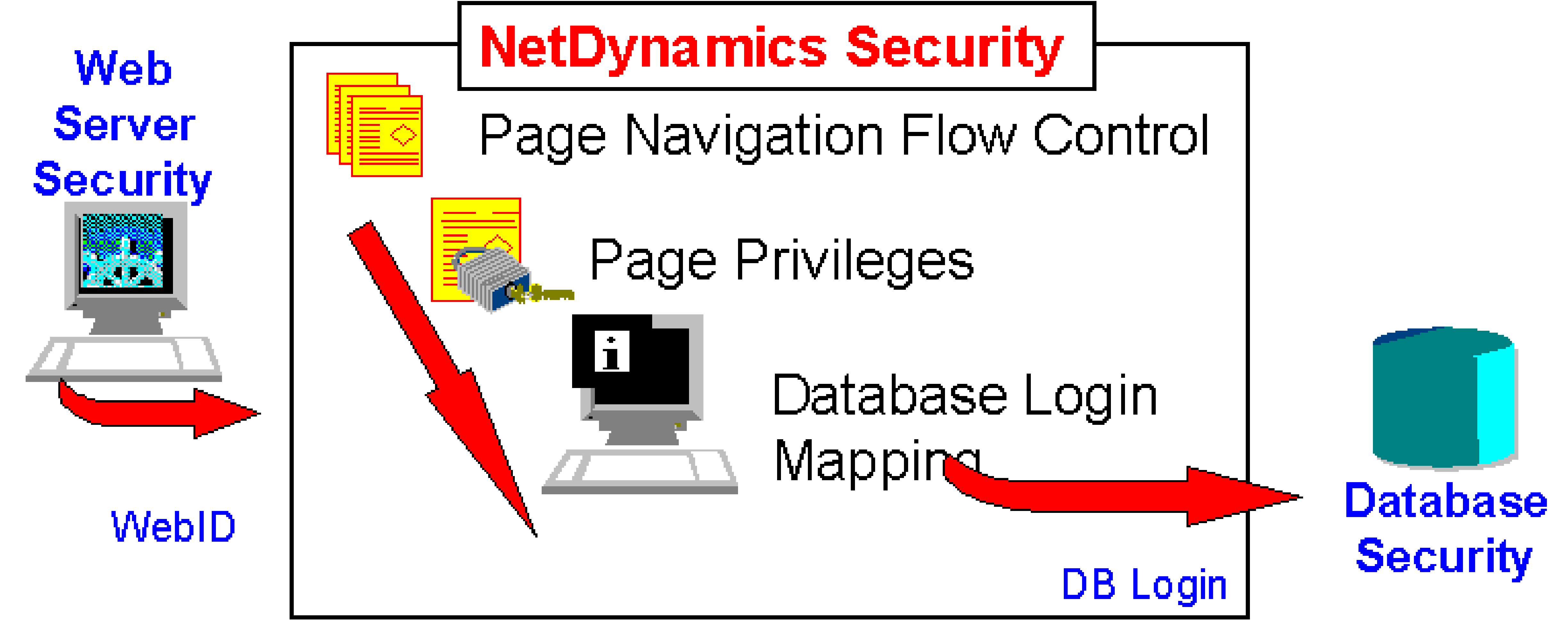
The following graphic is an overview of the security services provided by the ND Application server.

The idea of database login mapping allows the developer to take the web server user id and map it to a database login id. It is possible to map many web ids to one database login id and then be very specific about those ids that should have greater access. In this way you don't need to maintain a large database of database logins just a smaller table. We could for instance, map all "guests" to a common db login for querying only, map different departments to single department logins, or map each user to a unique database login (for auditing). By using many Web users to a few database logins we make maintenance easier, we make the likelihood of persistent DB connections very high and make the process more cost effective. The idea of making one Web user to One DB login mapping allows each db user to be monitored but DB connections will likely not be persistent.
Page
Flow Control
Page Flow control is used for imposing order on the application, so that
a user can't get to one page without going through another. This can be
good for forcing creation of necessary session objects, preventing users
from setting bookmarks and returning to a page without logging on. This
provides for "application flow" by pre-defining the information flow for
the users.
You can also define a page that is the startup page which is displayed
when the URL only contains the project name. One of the nice things about
the middleware development environment is that it will keep track of whether
or not the user has been to the pages. If a page flow violation occurs,
a security check failure event is generated which allows the developer
to decide what to do (typically send the user back to the first missing
page -- login for example).
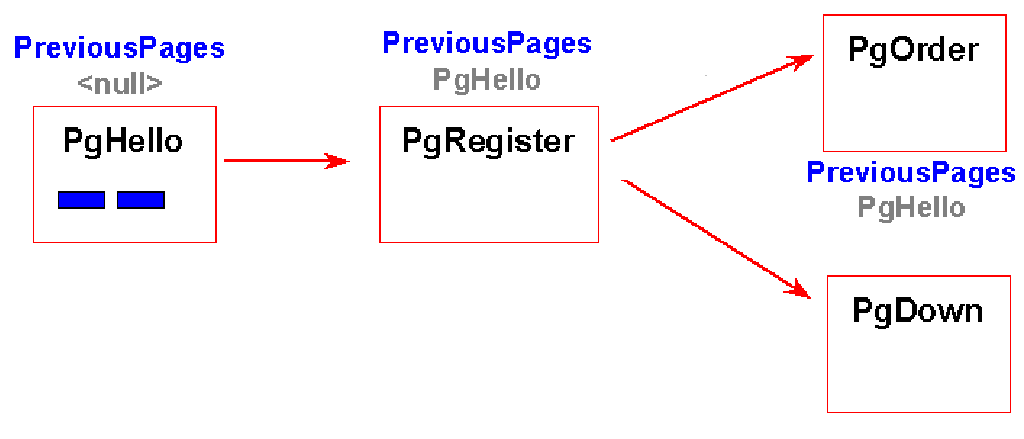
In the following example User starts at PgHello and can then go to
PgRegister. They must have been at PgHello in order to load PgOrder or
PgDown. Since they must have been to only pgHello, it is possible for the
user to miss PgRegister. The page flow is based on session activity and
so is only valid for the current session ID.
User Profiles
ND maintains a User Profile object for each user session which, oddly enough,
contains information about the user. This information can include Security
Object Activated flag, previous pages list, Web user Login name and password
(password can't be forwarded), DB user name and password) User Privileges
list, Remote IP address, Remote browser type. The Privileges are
stored in the profile to determine if a user can access specific pages.
These privileges are developer defined. A user's profile must contain all
the privilege tokens found in a page's privilege list to access that
page. The profile can be manipulated using the API to access/Modify current
privileges and current database logins via the profile handle and then
reset the profile.
The Security Object in
ND
The Security object is responsible for populating the user's profile with
privilege and database login mapping information. Fortunately there is
a wizard for defining the security scheme. The security object will automatically
retrieve and use information as the project is used by users.
Security Events
The Security Object Activated flag tells nD whether or not a security look
up has occurred. It is a property of the User Profile. Once the security
look up has occurred for the session, the flag is set to true. If this
flag is False, the next isLoginRequired page will cause a security lookup
to occur. This allows the developer to force another security look up by
dynamically setting the flag to false. The event that triggers this is
the onSecurityLookupEvent(). Other events that can be used
by the developer are doPrivLookup(CSpUserProfile userProfile) which
expects the User Profile object to have the privileges populated. doDBLoginLookup(CSpUserProfile
userProfile) which expects the user profile object to have the database
logins populated.
The developer has complete control of where the security information is obtained. It could be retrieved from an external security application or Internal business login based on the login id.